
Lessons learned and industry resilience from CDK cyberattack, David Kain
Cyberattack on CDK Global sparks urgency for auto dealerships to enhance cybersecurity measures. David Kain advises on crisis management strategies.
7939 NW 21st St
Miami, Florida

Cyberattack on CDK Global sparks urgency for auto dealerships to enhance cybersecurity measures. David Kain advises on crisis management strategies.

Investors should pay close attention to the vulnerabilities of AMD stock amid the AI boom and potential value destruction.
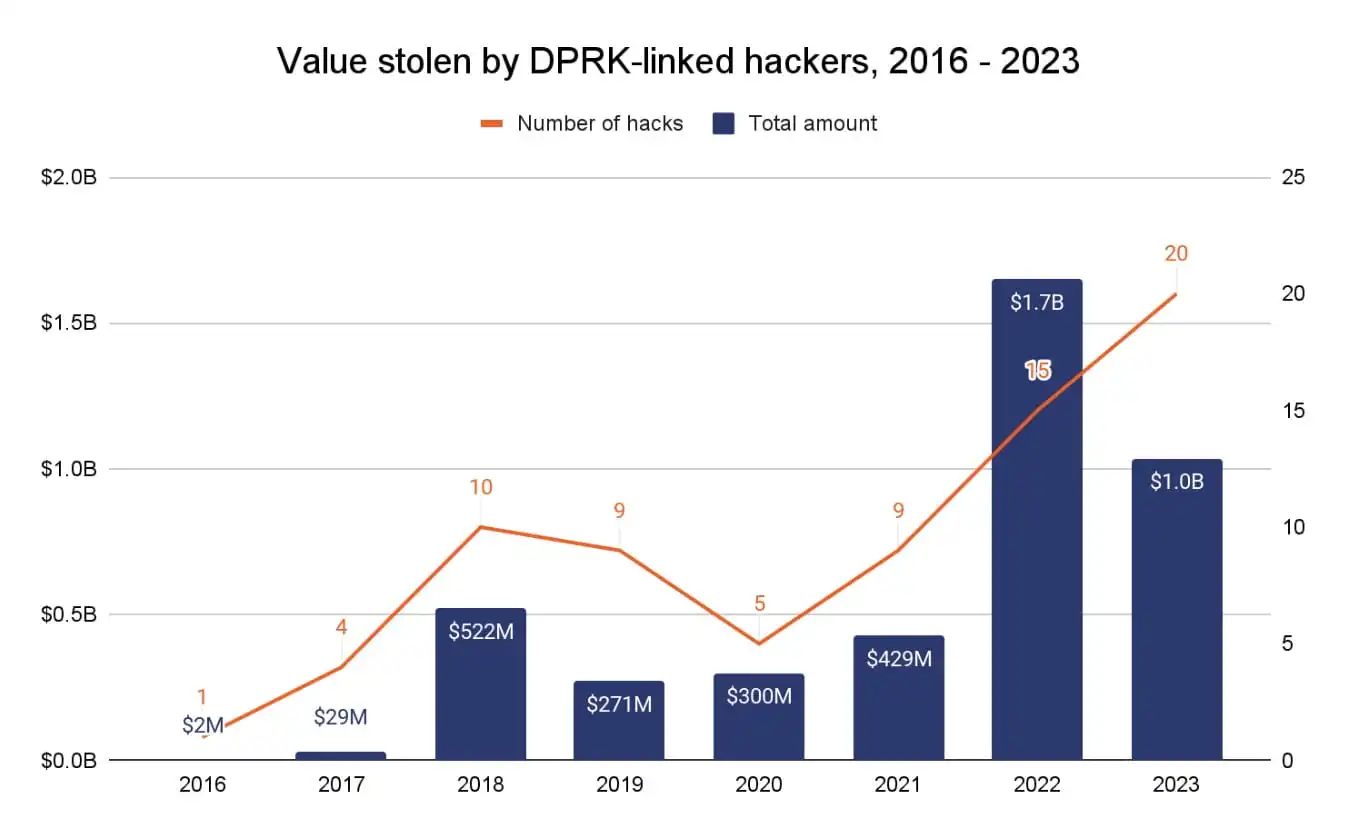
North Korea-linked hacking groups stole less cryptocurrency in 2023 despite more attacks. Chainalysis predicts more sophisticated and diversified cyber attacks.

Delta Dental of California reported a data breach affecting 7 million patients, exposing personal data through the MOVEit Transfer software.

Chipmaker Nvidia and seven other companies have agreed to a set of artificial intelligence (AI) standards led by the White House. The standards include requirements to disclose AI-generated content, share vulnerabilities, and commit to external testing before releasing products. The companies joining the agreement include Adobe, Palantir, IBM, and Salesforce. The White House has been engaging with industry on AI development and is promoting steps to ensure AI safety and security. The agreement will go into effect immediately and requires companies to prioritize research into minimizing harm and addressing security challenges.
Hey there! Ever wondered what’s lurking in those news headlines when you search for 'vulnerability' in computing? Well, grab your favorite drink and sit tight because we're diving into it. When we talk about vulnerabilities in the tech world, we're dealing with potential weak spots that hackers can exploit to wreak havoc.
Breach Reports: This is usually front and center. Every so often, a major company reveals they've been hacked due to some vulnerability they overlooked. Think of it as leaving your front door open while going on vacation; it's bound to draw unwanted visitors. These reports tell us which companies were targeted, how severe the breach was, and sometimes even how many users are affected.
Patches and Updates: Another dominant theme you'll notice is software patches. Companies like Microsoft, Google, or Apple release updates to fix known vulnerabilities regularly. It’s like putting up stronger locks after realizing someone knows where you hide your spare key under the doormat!
Emerging Threats: You’ll also come across cautionary tales about newly discovered weaknesses—in systems both old and new—coming from security researchers or ethical hackers who spend their days digging into code looking for flaws before the bad guys find them.
User Awareness Campaigns: Now more than ever, you'll find pieces stressing the importance of staying informed about online safety practices: using strong passwords (no more “password123”), enabling two-factor authentication, avoiding suspicious emails—you know the drill.
'Zero-Day Attacks': Lastly but importantly—zero-day attacks pop up quite heavily too! Zero-days are especially sneaky vulnerabilities unknown until someone exploits them perfectly out-of-the blue—a real curveball for any cybersecurity team!
The next time you're munching on tech news over breakfast tacos or scanning headlines during lunch breaks—with these juicy tidbits—we promise reading will never be boring again!